Static Application Security Testing Explained Simply
The primary objective of static security application testing is to detect and eliminate vulnerabilities as early as feasible in the application development process. But what’s the big deal about this?
As technology develops, so does the number of cyber threats that businesses must manage. According to experts, the cyber risk may “delay the rate of technology software’s source codec innovation by as much as US$3 trillion in lost economic value in 2020.”
Mitigating the growing cyber risk gap and helping businesses to realize the full potential of emerging technologies is a defining issue of our day. Security application testing is an important component of this pursuit.
Application security testing may be split into two categories, according to Transparency Market Research.
- SAST: static analysis of an application’s source code with database access. SAST is often implemented through white-box software testing.
- DAST: dynamic analysis of the running application using the black box software testing method.
- IAST: It covers testing for interactive application security with source code and execution environment access. In this case, white box testing is also used.
- MAST: MAST encompasses all mobile app security testing.
Using SAST as a case study, let’s go deeper into these issues.
- What is static analysis?
- What are the necessary resources and procedures for conducting SAST?
- What are the most efficient strategies for implementing it?
- Is SAST a must-have, or can you do without it?
What is static analysis?
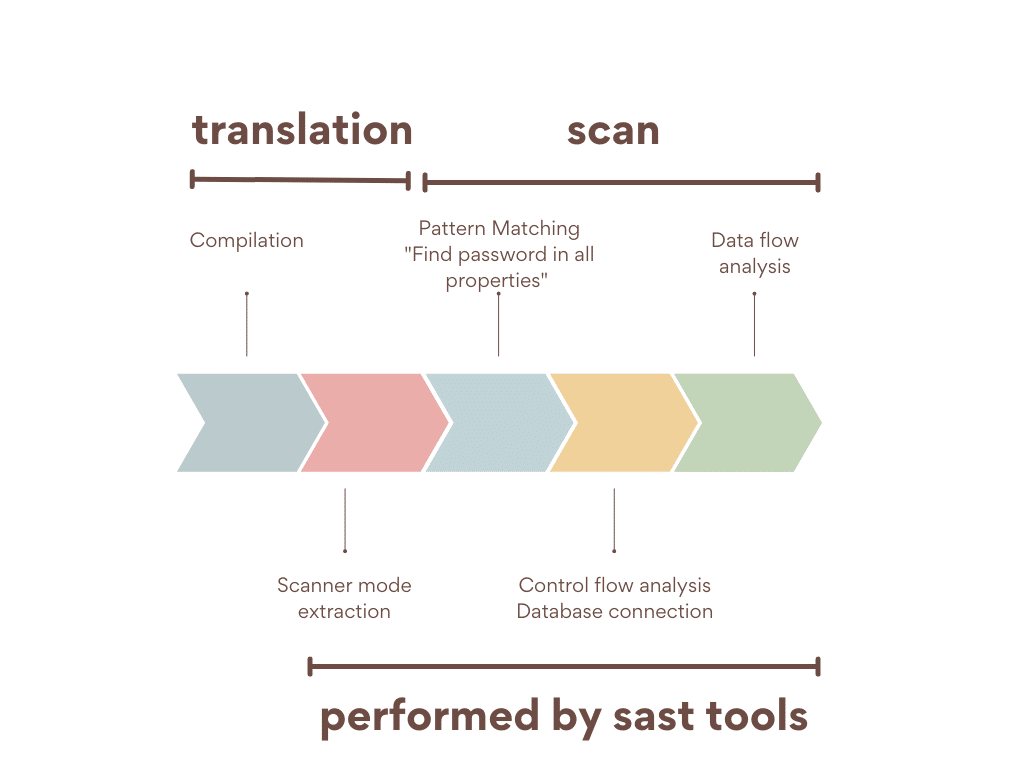
Static application security testing (SAST) examines the source code of the software to find potential security flaws before the software is released. SAST employs white-box testing to locate the source of security problems and then works to fix those flaws.
Rather than running an application to check for vulnerabilities, SAST (Static Application Security Testing) examines the source code or a portion of it. It verifies that specifications and standards are being followed without executing any code.
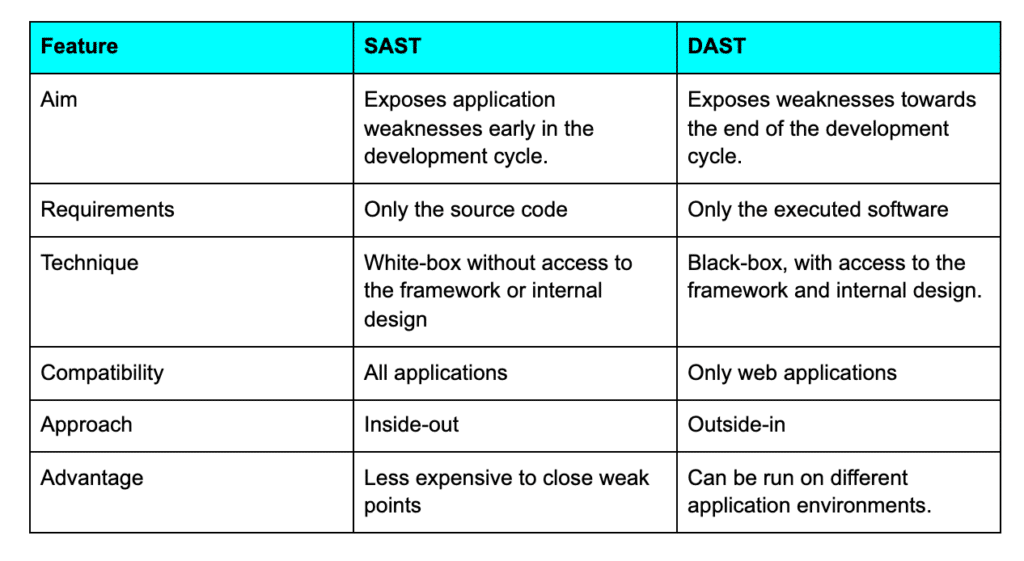
What’s different between SAST and DAST?
Testing techniques, such as SAST and DAST, have different advantages. In various periods of the software development life cycle, they discover different kinds of vulnerabilities and are most successful in doing so.
Static testing may be used in the early stages of an application’s lifecycle whereas dynamic testing can be used in a runtime environment to test fully-fledged code. SAST and DAST should be included in your application security testing program since this is the most effective strategy.
To see how they compare, look at the table below.
What are the advantages of STAT?
According to Grand View Research, application security will generate $10.7 billion in revenue by 2025, growing at a rate of 17.7 percent annually. This implies that testing methods like SAST are increasingly becoming more important for organizations who want to maintain. Here are the reasons why.
Flexibility
SAST’s broad support for programming languages and development platforms is an important asset. Static code analysis tools are available from a variety of vendors for almost every popular programming language.
Handy
SAST is simple to use — adding a static scanner to your development process, and IDE is no problem at all.
Thorough testing
With the STAT method, the software is thoroughly tested for coding flaws and security vulnerabilities early in the development process to guarantee trouble-free deployment later on. These tools can look for errors in an application even if it is still in a basic stage without executing it.
Saves time and effort
In most organizations, development teams outweigh security staff, making manual code reviews very difficult, if not impossible. Millions of code strings may be scanned in minutes using SAST, which fills the void. By using the SAST that meets all of the specifications, you’ll be able to find bugs in your code with more precision and spend less time and money fixing them.
Precision
Static source code analysis is useful to developers since it pinpoints the precise position of a possible issue. For example, it highlights sloppy portions of code and gives immediate feedback regarding programming errors in an understandable manner. Some of these tools also provide practical advice on how to deal with the problems they’ve uncovered. Creating customized reports creates another level of visualization to the process, making it simpler to monitor faulty codes and facilitate the remediation procedure.
Hosting options
Static application security testing tools may either be deployed on-premises at the client’s location or be hosted in the cloud (software-as-a-service). However, it’s worth noting that while on-premises deployment gives you greater control over the solution and its capabilities, it typically comes at a higher expense in terms of upkeep than a cloud-based setup.
What are the disadvantages of STAT?
SAST is not particularly good at identifying faults in the data stream; instead, it does the greatest job of finding mistakes in long code snippets.
There are a lot of false positives and negatives when using SAST. This is because static analysis takes a long time since engineers have to manually filter and verify each piece of software that may be susceptible.
New requirements and changes should be made to the existing environment to reduce the number of false positives.
Another drawback to conducting static security tests is that they are ineffective in dynamic environments. The test reports also easily become outdated since the method is primarily static.
What are the characteristics of static application security testing?
SAST must provide the following characteristics:
- Deep code analysis and vulnerability detection are now possible because of the availability of high-quality tools and algorithms.
- Updated and versatile rule foundation with customizability and extensibility.
- Detailed reports with evidence-based suggestions on how to fix the vulnerabilities that have been found.
- Comparing the analysis results when the modified code is rescanned (highlighting patched, unpatched, re-emerging vulnerabilities).
- A broad range of programming languages is supported.
- Adaptability to a variety of development and testing environments, including version control and bug tracking systems.
- Developer and security expert communication.
- As few false positives as possible.
- Easy-to-read presentation of the findings from the analysis.
- Automated reporting technologies are readily available.
- Remote code analysis
What are the necessary resources and procedures for conducting SAST?
The following are the best software for security application testing
- CxSAST Checkmarx
CxSAST by Checkmarx automatically discovers security flaws in uncompiled code written in the most widely used programming languages. There are two ways to use CxSAST: as a stand-alone application or as part of the software development lifecycle (SDLC).
The following are some of its strongest points:
- Code visualization in the form of execution path operation charts.
- Recommendations are provided on how to address graphic scheme linking issues based on scan findings.
- There are 27 programming languages supported by this tool.
- Built-in support for several development environments (such as Eclipse, IntelliJ, and Visual Studio) as well as build servers, version control systems, and bug tracking (Atlassian Jira, etc.).
- Static Code Analyzer for Fortify (SCA)
Over the course of its lengthy existence, the company that now supports this software has gone through numerous ownership changes. In the meanwhile, it’s evolved into a potent source code analysis instrumentation tool.
In the Fortify product line, the Static Code Analyzer is a static application security testing module. It pinpoints the root causes of security flaws, ranks the severity of the findings, and makes specific fixes for the code in question.
The following are some of its strongest points:
- Python, ASP.NET, and Ruby are just a few of the 21 programming languages supported.
- Comprehensive vulnerability coverage, including the Top 25 SANS vulnerabilities and Top 10 OWASP vulnerabilities, along with compliance with DISA STIG and PCI DSS.
- Model for threat intelligence that works both on-premises and in the cloud.
- It is possible to connect with continuous integration management systems and generate error reports automatically.
- Reduces false positives using machine learning techniques.
- HCL AppScan Security by HCL Technologies
For information security experts, HCL Security AppScan Source (previously IBM Security AppScan) is developed. It is difficult to use and requires advanced training. The tool facilitates communication between security professionals and programmers. It includes tools for integrating with popular development environments so that vulnerabilities may be discovered early on.
The following are some of its strongest points:
- Over 40 distinct templates are available straight out of the box for general, and compliance reports.
- There are 21 different programming languages available.
- Preventing data breaches and assaults on web applications is made easier with AppScan Standard, which runs a continuous risk assessment as soon as the website is put into operation.
- The AppScan eXtension Framework offers fine-tuning and upgrades possibilities.
- AppScan’s SDK allows for easy integration with current systems.
- There are link classification capabilities that may be used for purposes other than app security, such as assessing the danger of users accessing undesirable sites.
- Aids in identifying which site technologies have the potential to influence the results of an AppScan crawl.
Best practices for conducting static application security analysis
SAST may be performed effectively in six stages. These include:
Choose the tool
Opt for a static analysis tool that can code examine apps produced in your preferred programming languages. The tool should also understand the software’s underlying structure.
Set up the scanning system
This phase handles licensing, access control, and permission and acquiring the necessary resources (servers, databases).
Sync the tool with your requirements
Customize the tool to meet the organization’s requirements. You may write new rules or update current ones to minimize false positives or discover new security issues. Create custom reports and dashboards to monitor scan findings.
Determine application priority
Onboard your apps once the tool is available. If you have a lot of apps, check the riskiest ones first. Onboard and scan all of your apps, with scans synchronized with release cycles, daily or monthly builds, and code check-ins.
Examine the key findings
Triage the scan findings to eliminate false positives. Once completed, problems should be recorded and given to the deployment teams for prompt repair.
Provide leadership and training
Your development teams will use the scanning tools correctly if you have adequate governance. The SDLC should include software security touchpoints. SAST should be used in application development and deployment.
Is SAST a must-have, or can you do without it?
Organizations must conduct security testing at all times. Static analysis is essential if you want to keep on top of the ever-changing tech landscape while also decreasing the risk to the security and privacy of your application. In the world of cybersecurity, faults and vulnerabilities in software are major causes of concern. It is possible to reduce risks by using SAST solutions instead of outsourced professionals.