Imagine a world where your alarm clock seamlessly communicates with your coffee machine, which then coordinates with your car to prepare a fresh cup of coffee just as you’re ready to leave for work. This interconnectedness, made possible by the IoT, has revolutionized our society, extending its reach to our homes, hospitals, office buildings, and beyond.
The Internet of Things, or IoT, might be one of the fastest-growing avenues in modern technology. At the same time, it is one of the most widely misunderstood. Broadly defined, the Internet of Things facilitates communication between various machines and other objects, allowing them to coordinate with one another to perform a wide variety of functions. That said, the fast development of the IoT amid growing cybersecurity issues has led to widespread concern regarding a world of interconnected devices and user privacy.
In this article, we’ll take a look at different layered architectures of the IoT and discuss security from the perspective of those layers. At the same time, we’ll review a series of mechanisms that claim to provide solutions to such security issues. Lastly, we’ll suggest a new layered architecture specifically designed to overcome these problems.
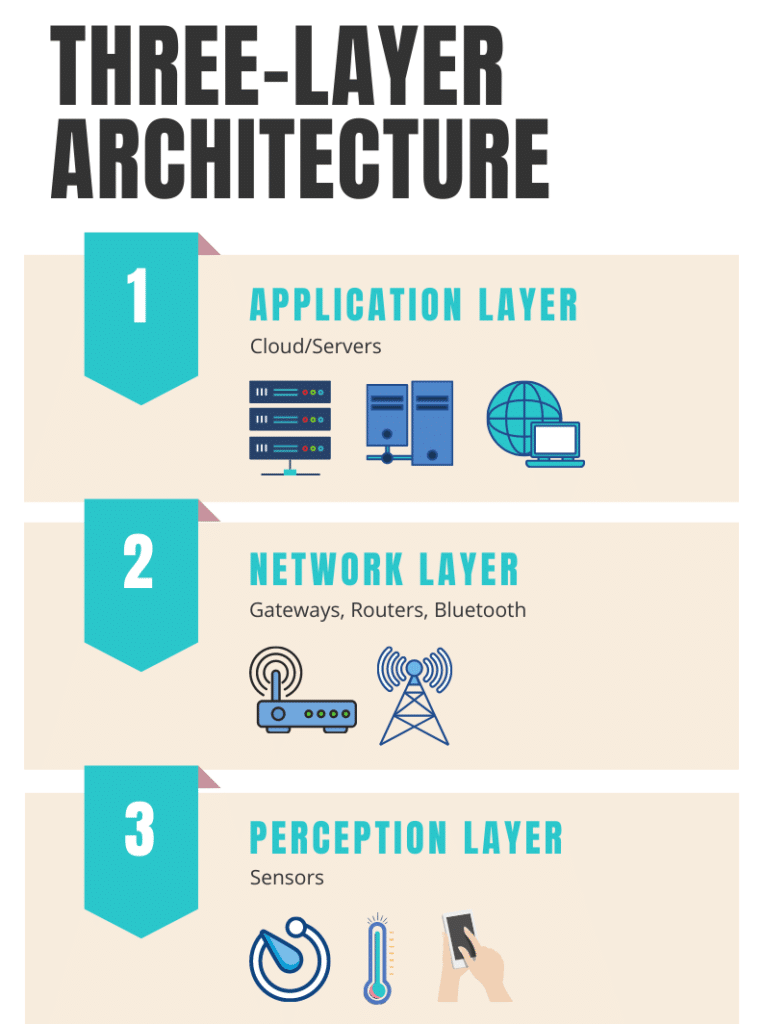
What are the 3 levels of IoT architecture?
The most basic architecture associated with the IoT is known as a “three-layered” architecture. Introduced in the early stages of research into this topic, it consists of the perception, network, and application layers.
- The Perception Layer – This is the physical layer. It has sensors for finding and gathering information about an environment, including the ability to identify other smart objects.
- The Network Layer – This layer connects to other smart objects, including servers, network devices, and more. It can also transmit and process sensor data.
- The Application Layer – This layer is responsible for actually providing application-specific services to the user. It does so by defining ways to deploy the IoT, such as in smart homes or smart cars.
The three-layer architecture is undoubtedly a fundamental concept in the realm of IoT and serves as a basis for much of what is currently available in this field. However, while it provides a useful framework, it may not offer the full breadth of understanding needed for comprehensive research into the IoT. Hence, there is a growing interest in exploring alternative layered architectures like 5 layer architecture of IoT.
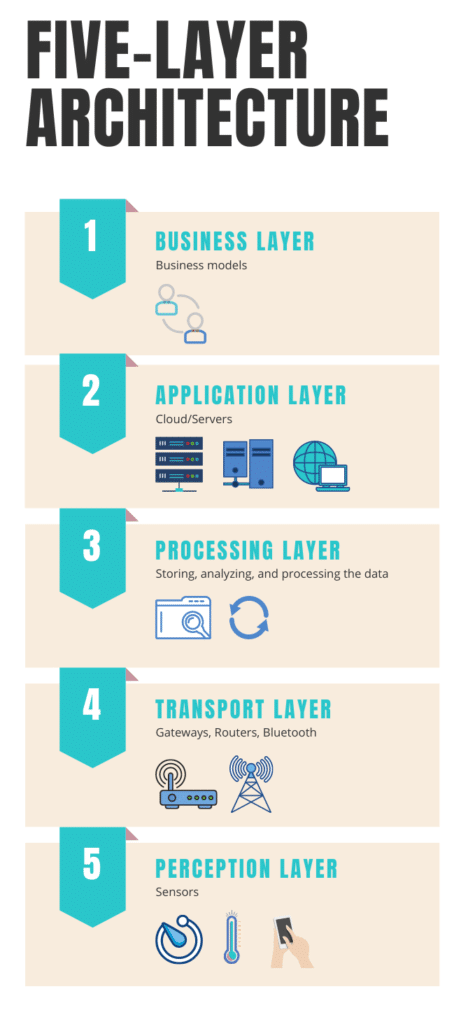
What are the 5 layers of IoT architecture?
Our five-layer architecture of IoT forms a layered network comprised of perception, transport, processing, application, and business. In this model, the roles of the application and perception layers do not change. The three remaining layers, however, operate as follows:
- The Transport Layer – This layer is responsible for transferring sensor data from the perception layer to the processing layer. It utilizes a variety of networks, such as RFID, Bluetooth, and 3G, to do so.
- The Processing Layer – also widely known as the ¨middleware layer¨, is responsible for storing, analyzing, and processing the data it receives from the transport layer. At the same time, it can manage and provide various services to the lower layers, employing technologies ranging from cloud computing to big data processing modules.
The Business Layer – This layer is designed to manage the whole IoT system effectively. It includes everything from applications to user privacy to business and profit models.
What are the issues in 3 layer IoT architecture?
In order to have a detailed discussion about three-layer IoT Architecture, its benefits, pros, and cons, it’s important to go further than our initial identification of the associated parts.
The Perception Layer
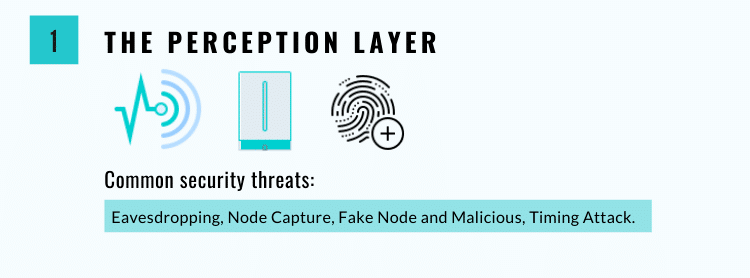
Also known as the sensor layer, this layer acts much as a human’s eyes, nose, or ears would. It is responsible for identifying objects and collecting information from them using RFID, 2-D barcodes, and other types of sensors. Data collected by these sensors can include everything from motion and location info to changes in the air or environment. These sensors are a popular target among attackers, whose goal is often to replace them with a sensor of their own.
Common security threats associated with the perception layer include:
- Eavesdropping – This is an unauthorized attack that takes place in real-time. During this attack, the attacker seizes private communications : phone calls, text messages, video conferences, and faxes are seized by the attacker. This data is ultimately intercepted over a network, which may or may not be secured.
In 2022, security researchers discovered a vulnerability in the Bluetooth Low Energy technology used in Tesla’s entry system, enabling attackers to potentially remotely unlock and operate the vehicle. While the attack was demonstrated on Tesla vehicles, any vehicle that uses BLE for keyless entry could be vulnerable. - Node Capture – This is one of many harmful attacks that can affect the perception layer of IoT devices. Through node capture, an attacker can gain full control over a key node, such as a gateway node. This allows the attacker to leak a variety of communications between the sender and receiver while gaining access to information stored in the device’s memory. This could result in identity theft and fraudulent transactions.
- Fake Node and Malicious – This is when an attacker adds a node to a system that is designed to input fake data. This attack aims to stop the node from transmitting real information, consuming energy from authentic nodes, and potentially destroying the network.
A real-life example of a fake node attack happened with a cryptocurrency mining pool NiceHash. The hacker added a fake node to the mining pool, which reported false information about the computing power of its miners. This caused the mining pool to assign computational tasks to the fake node, resulting in other legitimate miners wasting their resources on fraudulent work. As a result, the attacker could earn a significant amount of cryptocurrency without contributing any actual computational power. - Replay Attack – Also referred to as a “playback attack,” this is where an attacker eavesdrops on a conversation between a sender and receiver and steals information from the sender. They then send this information to the victim in an attempt to prove their authenticity or as “proof” of their identity. Once they’ve assumed the real sender’s identity, they can then entice the recipient to perform any number of actions.
For example, as mentioned in a report by The Vice, hackers have found a way to use voice bots to steal sensitive codes from users in order to access their accounts and perform fraudulent transactions. By tricking users into revealing their 2FA or OTP verification codes, hackers can use these codes to login, make money transfers, or perform other sensitive actions. The voice bots are designed to sound like authentic customer care agents, making it difficult for users to detect the scam. - Timing Attack – This is particularly effective against devices that have weak computing capabilities. It allows an attacker to identify vulnerabilities in the system, bypassing them in order to steal information. To do so, they observe how long it takes the system to respond to a specific input, queries, or algorithms.
For example, an attacker could submit different password guesses and observe how long it takes for the system to reject an invalid password compared to a valid password, allowing them to guess the correct password with a high degree of accuracy.
The Network Layer
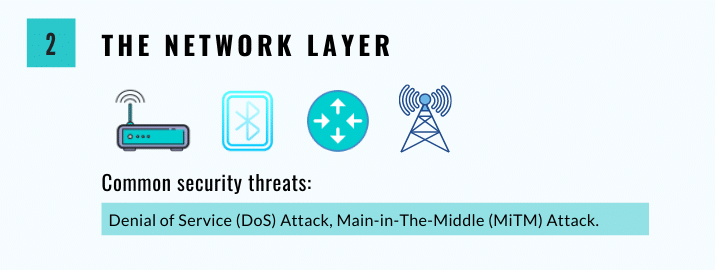
Also commonly referred to as the “transmission layer,” the network layer acts as a sort of bridge between the application and perception layers. Typically, it carries and/or transmits data collected by the sensors via wired or wireless means. It is also responsible for connecting the various “smart” items, networks, and network devices to one another. This causes it to suffer from many security issues related to information authentication and integrity.
Common security threats associated with the network layer include:
- Denial of Service (DoS) Attack – DoS attacks attempt to prevent users from accessing their devices or other network resources. It is most often accomplished by flooding targeted devices with so many requests that it becomes impossible for usersactually to filter them.
The importance of protecting against DoS attacks on IoT devices was demonstrated in February 2020 when Amazon’s AWS Shield service successfully mitigated the largest DDoS attack ever recorded, which measured 2.3 Tbps. - Main-in-The-Middle (MiTM) Attack – MiTM attacks take place when a third party intercepts and then alters communications between a receiver and a sender, changing the messages to suit their own needs. This signifies a major security breach, as it allows the attacker to manipulate information in real-time.
Let’s say you log in to your bank’s website using your username and password to access your account information. However, a hacker is intercepting your communication with the bank’s website using a MiTM attack. The hacker could modify the communication in real-time, such that any money transfers you initiate are redirected to the hacker’s account instead of the intended recipient. - Storage Attack – A user’s information is usually only stored in the cloud or in various storage devices. Both of these can be attacked by outsiders, with users changing information at will.
In 2020, SolarWinds was the target of a major storage attack that resulted in the distribution of a remote access trojan (RAT) known as Sunburst. More than 18,000 customers of SolarWinds had applied the Sunburst update, which then allowed the RAT to infect all their customer systems and networks. - Exploit Attack – This is where an attacker takes advantage of security weaknesses in a system, application, or hardware. The goal is most often to steal information stored on a specific network. Attackers may use a variety of techniques to identify and exploit these weaknesses, including scanning for open ports, sending malicious payloads to specific network addresses, or using social engineering tactics to trick users into downloading malware.
The Application Layer
The Application layer defines all of the applications that utilize IoT technology or in which the IoT is deployed. This includes smart homes, smart cities, etc. Its goal is to provide services to various applications as sensory information demands. The application layer suffers from various security issues, particularly in the cases of smart homes and smart offices. This is especially true of smart devices that have weak computational power and low storage capabilities.
Common security threats associated with the application layer include:
- Cross-Site Scripting – This is an injection attack that enables a third party to insert a client-side script in a trusted site. This eventually allows the attacker to change the application’s contents according to their needs or to use the original data illegally.
By exploiting vulnerabilities in the code, attackers can steal users’ sensitive data, such as login credentials and credit card information, or redirect them to phishing sites. To prevent cross-site scripting attacks, website owners should implement input validation and output encoding, and users should keep their web browsers and plugins up-to-date. - Malicious Code Attack – This is code embedded in software designed to cause damage to the system. It can take many forms and affect devices at all levels of the IoT architecture. This attack is extremely common and can often be blocked by antivirus or anti-malware programs.
Final Thoughts
IoT is quickly weaving itself into modern life all around the world. By connecting smart devices, applications, and other technology, it has the power to enhance our quality of life and automate a near-infinite number of interactions.
Still, we hope this brief overview has properly outlined how layered architectures of IoT can be subject to specific, malicious attacks by third parties. Our goal is simply to remind leaders that, while the possibilities of the IoT are indeed exciting, proper precautions and security measures must always be taken.
Moreover, it is important to consider new multi-layered architectures in order to design a more secure infrastructure for the IoT. Ultimately, it is our hope that we can encourage more users to address these problems and implement the necessary changes as soon as possible.









