Architecture & Development
The development of secure cloud-native applications involves more than just the technological angle, it relies on the people involved and the process executed to allow faster and more innovative delivery of applications for an organization.
By taking advantage of cloud computing models, secure cloud-native applications assist in the more flexible and rapid development, while increasing output quality and mitigating risks at the time of deployment. Though its namesake may imply otherwise, cloud-native methods are not geared to the target of application deployment, but rather on the process of how they are built, managed, and deployed.
This development and distribution approach combines microservices, contemporary self-contained API-based infrastructures, and leveraging of DevOps that promote the continuous delivery of applications. Microservices and applications are often conflated in discussions, but organizations are able to achieve optimal application development results by turning their focus on building superior, monolithic apps by utilizing similar principles. These include:
- Tech-agnostic, light API intercommunication between design components
- Self-contained infrastructure with the rapid deployment of services and apps that are both portable and can be scaled to meet the demand for particular capacities.
- A service-centric architecture that is coupled loosely
- Utilization of both build and delivery focused DevOps practices geared at collaborative application delivery, as well as CI/CD (continuous integration and delivery) Agile methods.
The Benefits & Challenges Of Cloud-Native Architecture
The cloud-native architecture permits the achievement of the speedy and agile app development tactics based on a methodological design that uses various cloud services including Lambda from AWS, EC2, and S3. Rather than using a monolithic app infrastructure, it builds, runs, and updates software through a microservices suite of cloud-based tools.
Because there is no downtime of conflict in independent service deployment or inter-provider cloud transfer regardless of language or framework, the containerized nature and use of microservices promote the fast and agile nature of the process.
Microservices are primarily functional in promoting efficient collaboration and productivity. This allows various DevOps departments to independently work on various components of the same application simultaneously. Even more prudently, they are able to implement new enhancements and features with the application stability remaining unaffected.
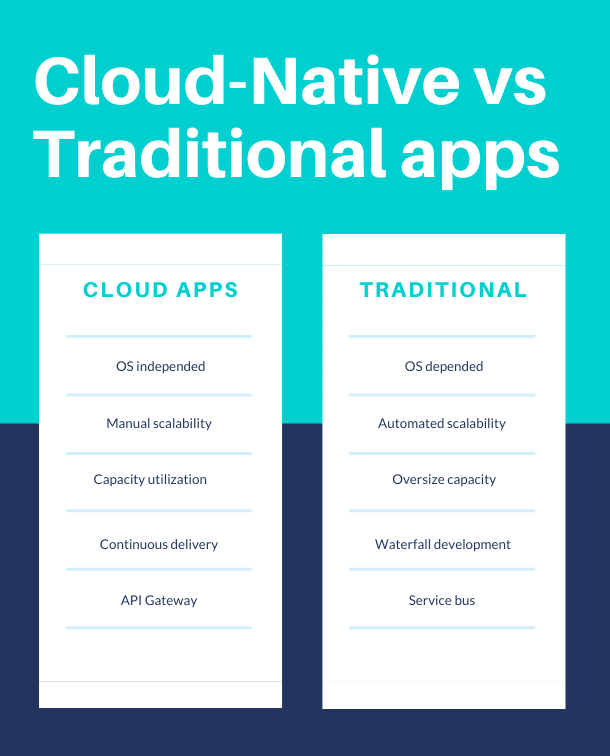
Getting Better Results During The Development Process With Cloud-Native Architecture
Cloud-native application architecture is capable of delivering better results during the application development process with architectures suited specifically for faster, more frequent releases of complex applications. Among some of the architecture, attributes are the utilization of microservices, containerization, automation using DevOps, enhanced agility and scalability, and the shortening of time-to-market.
Microservices Architecture
Leveraging microservices architecture is advantageous as it allows for simultaneous advancement of varying parts of a project. The concept of microservices is breaking a larger project down into a more modular model that communicates with other microservices via APIs. This model essentially splinters up a big project into smaller, independently functioning shards, and solves multiple problems that plague large monolithic projects. If one module has a problem, it does not hold up the entirety of the development of an application and an individual part of a whole is easier to understand on a deeper level. They also take less time to deploy and are far easier to scale piecemeal.
Containerization
‘Containers’ include the application itself as well as all the tangential components that are needed to have it function in isolated environments in either a virtualized environment or on a traditional operating system. By self-containing, all the pieces of a bigger enterprise allow for much greater agility for developers to integrate applications in the DevOps environment. By having applications in their own ‘containers’ they can start up quicker, be deployed in shorter time periods, and have the installation more easily managed, as everything is packaged together to promote efficacy and expediency.
Automating with DevOps
The slowest part of an installation process is typically the human performing it. By automating the application with DevOps, the necessary human assistance is lessened, thereby speeding up operations. It allows development teams to issue and deploy updated application versions faster and enhance the application more effectively.
Enhanced Agility And Scalability
With the freedom of cloud-native application development, the process experiences added agility as it promotes faster innovation and enhancement expansion of the application in a shorter span of time. With the life cycle of the application development shortened, the developers can focus on ways to help the application grow, scaling its usage, a huge advantage in a realm where competition is ever-increasing.
Reduced Time-To-Market
Time-to-market is the time that it takes from the conceptualization of an application to its eventual sales. The shorter the time-to-market, the faster the benefits of the design can be offered and profited from. However, something overly large and complex turned over fast too quickly is sure to come out of the development process with insufficient testing, lack of features, options, and lack of intuitiveness. With cloud-native development, the time-to-market is shortened as there is a finite area of concentration for the developers to hone in on. That means there is a greater focus on the areas that make that particular module feature of the entire application, yielding far higher quality. Higher quality earns a good reputation with consumers who then convert the application with additional sales.
Cloud-Native Security
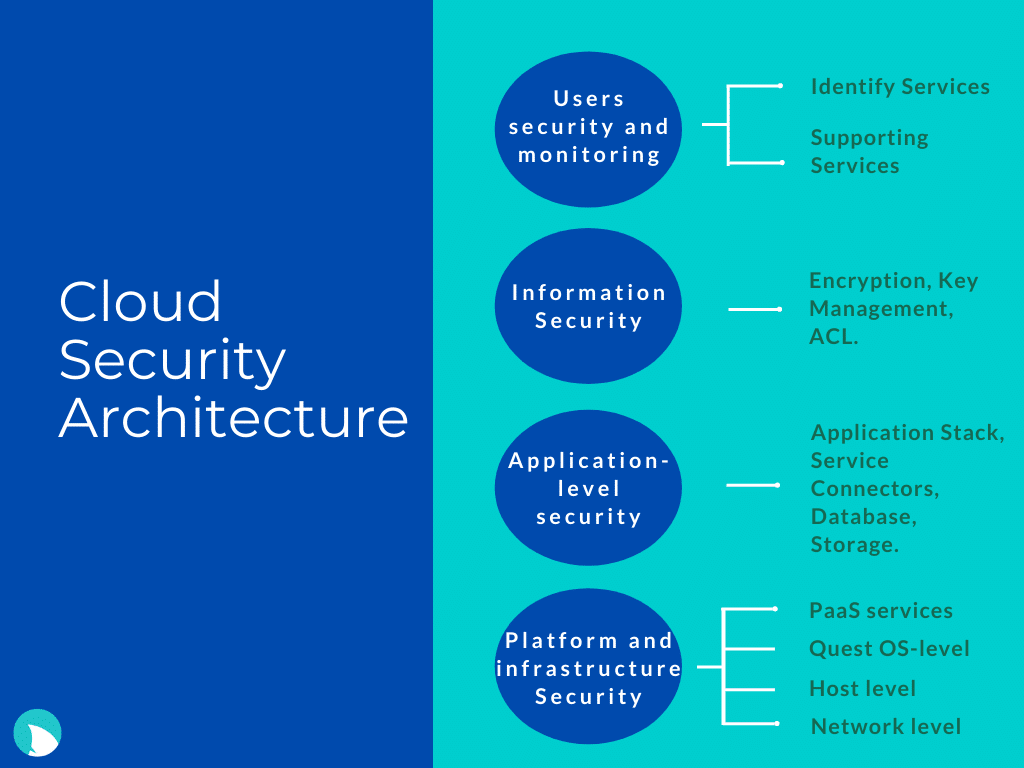
Traditional application development approaches burden the developing organization with securing not just their software, but their tools and the development facility as a whole. Cloud-native application development alleviates some of these burdens. But organizations must understand the coverage of all areas of their application and whose responsibility it is to address various security concerns. If the responsibilities are clear, greater concentration can be given to the various aspects of the application.
Security is not a one-shot deal, but rather a continuing, iterative evaluation and a process of adapting and adjusting. Security concerns are uncovered, noticed, and encountered perpetually, with new exploitations arising frequently. That means that the aspect of security must be at the forefront of any support offered to an application long after it has been deployed.
Cloud-native development assists in not only greater concentration on areas that need to be addressed by parties responsible for security efficacy, but also provides the ability to push out security patches and new tools to support security measures quickly.
Security must also be multilayered, built into all levels of the design. Every hole that can be plugged on the operating system level, container level, and application-level must be defended. In order to do this, the design must be intricately understood, analyzed, assessed, and ultimately secured.
Challenges u may face while Building Secure Cloud-Native Applications
Without A Perimeter, There Is No Perimeter Security
A legacy approach to security involves containing the infrastructure behind walls, then observing and blocking potential external contaminants. However, shifting to serverless, cloud-native technology, eliminates the perimeter meant to be guarded. Consider API Gateway sourced functions. They will be protected by WAF, but if functions are from multiple event sources like cloud storage events, database alterations, stream data instances, and other varying event sources will not incur the same type of protection.
Firewalls and legacy scanner approaches tend to be insufficient in terms of security because perimeter defenses and scans do not possess enough insight and comprehension into the resources that are needing protection. When there is a lack of understanding, wrong conclusions are drawn, mistakes are made, and false-positive results. These need to be addressed by experts whose participation is required to identify vulnerabilities and plug the gaps that result in false negatives. These processes require a lot of human involvement, making the security process challenging to scale.
Dynamic Requirements Require Dynamic Security
There is not a one-size-fits-all method for application security. Applications that have newer, more distinct structures, require a security approach that is equally as distinct. Using the same approach is actually not feasible as it varies in terms of:
- Virtual machines
- Containers
- Containers-as-a-service
- Serverless functionality
High Fidelity Visibility And Context
The vastness of the cloud grows at a far more rapid pace than anyone’s ability to keep it secure, making visibility, regardless of the magnitude of fidelity, very tough. When visibility is limited, it lacks sufficiently broad context. This, in turn, often leads to flawed conclusions. When there is less visibility and less centralized administration, the chances of bad configurations and system flaws increase, and in that, so does the risk. When risk alerts are light on context, more manual, human involvement in the development process becomes required. This not only triggers eventual alert fatigue but results in delays while security risks are addressed.
In this lies the key problem that cloud-native security must address: context. It is not enough to just know the IP address from which suspicious activity was conducted, but also the user/group, content, protocol, destination, application functionality, etc.
The People, Processes, And Tech Of Cloud-Native Security
451 Research released a report that noted that the incorporation of AI, intelligence, data analytics, automation, and threat detection by organizations adopting cloud-native security, is necessary to deal with security gaps in an ever-changing digital ecosystem. The protection on all levels, as well as continuous, vigilant monitoring for new issues, must be fully integrated into the application infrastructure. It is important to recognize that the tools leveraged by organizations during their digital overturn are outpacing any security budgets, tools, and qualified staff to address these matters.
Functional Requirements for Secure Cloud-Native Applications
To engage in necessary cloud-native security actions, certain functional requirements need to be considered and actions that must be taken.
- Administrators and developers must be provided authorization and authentication that will allow them to access cloud resources.
- Microservices level will also need the appropriate access to operate on the cloud level.
- Network isolation, secured connectivity, and protection must be provided.
- Protection instituted against exploitation of application vulnerabilities and DDoS (denial of service attacks)
- The components on the processing, application, and memory levels must be fully separate
- Data should be guarded whether it is static, dynamic, unused, moved around, or currently utilized.
- Tools for scanning the system for vulnerabilities must be provided at both the application and infrastructure levels in order to ensure faster development and deployment of critical security changes and patches.
- To achieve full compliance, all API calls must be captured and stored, as well as to be viewable for auditing purposes.
- Security issues must be centrally viewed.
Final Thoughts
Security is an essential measure for any application development process. While cloud-native computing eliminates some of the security measures, there are doubtlessly still challenges to overcome. It is imperative to focus not only on the standard security assessments but to also address the necessary concerns specific to the security of cloud-native development in order to fully utilize the architecture’s power.
Article by Evgenia Kuzmenko











