Why Is Cybersecurity Mesh Architecture the Best Security Solution for a Fintech Company?
Gartner created the Cybersecurity Mesh Architecture approach to help organizations shift away from compartmentalized security toward a more collaborative and flexible approach. By splitting security functions and allowing them to interact through a set of supportive layers, Cybersecurity Mesh Architecture aims to make security more composable.
In recent years cybersecurity has become more and more crucial for organizations. The leakage of personal data of the users can cause a huge scandal damaging your reputation, not speaking about the system breakdowns and outburst of private corporal information, which may severely affect the work of your company and even damage the whole business. Software supply chain, usage of cloud platforms, IoT, and operational technology, together with breached data trade extend security attacks outside of traditional perimeter security. The cyberattacks become more cunning, as well as the popularization of remote work makes the system more vulnerable. Your data can be accessed from any location by multiple devices, so each of them can be seduced to the cyberattack, while most of the security is focused on the silo. This leaves a lot of gaps and weak points in the system. Due to this by 2025 the expenses caused by cyber crimes will reach $10.5 trillion, growing by 15% globally annually.

On average an organization uses 45 different solutions. Once an incident occurs, it takes 19 different tools to respond to it, most of it is made manually. Together with this, those who operate more than 50 tools find themselves 8% less able to detect attacks and their rate of responding to the attacks is up to 7% lower. The problem occurs because the tools are poorly integrated, thus the quantity of tools doesn’t improve the security system.
All of the abovementioned show that we require new security tools to keep the systems safe. Gartner, a technological research and consulting firm came up with cybersecurity mesh architecture, which enables the bringing of detached tools together. As a result, the organization can receive security alerts quicker and react to the attacks through centralized management.
As a response to the security issues caused by remote work, the integrated security structure offered by CSMA, will secure all the assets regardless of their location. The unified security ecosystem will decrease the financial loss in the security sector within an organization by approximately 90% by 2024, according to Gartner.
A mesh stands for strong interconnection among devices or nodes and this principle is used for creating a network of devices directly relying on wireless nodes. For example a mesh network can be applied to interconnect the IoT devices.
Reasons to use Cybersecurity Mesh Architecture in fintech
The financial technology industry shows rapid growth in recent years. The global fintech market is seen to grow by 13.7% and will reach $190 billion by 2026.
At the same time, the fintech industry is one of the most vulnerable to cyberattacks. Dealing with such data as money assets and transactions makes the sector attractive to cyber attacks. According to an IBM research report, financial services have been the main target of cybercriminals for the past three years. The most widespread attacks are performed by ransomware and artificial intelligence to steal data. Access points are another vulnerable target for the attacks, as the result of the growing use of mobile devices for performing business operations. The traditional security perimeter doesn’t work anymore, as the data is dispersed and users are located worldwide. This challenge of the modern time nudges to implement new security solutions.
And the answer to these new challenges is cybersecurity mesh architecture. It corresponds the best to the need for protection of all the devices, instead of being concentrated only within the silo. According to CSMA, the integrated security structure is deployed where it’s most needed, regardless of the user’s location. So as the remote work and multi-cloud solutions are here to stay with us for long and intent to even evaluate, the sooner CSMA will be implemented into fintech the sooner you will benefit from it and reduce the cyber security tension.
With all the benefits of Cybersecurity Mesh Architecture we have discussed, let’s figure out more precisely the main principles of CSMA and how it works.
How Cybersecurity Mesh Architecture works
First of all cybersecurity mesh helps to implement zero-trust to secure data and systems as a whole. As the data is no longer stored just within the organization’s network all of the connections are considered unreliable before they are verified. CSMA aims to protect every device and access point giving each asset within an infrastructure its own perimeter, rather than creating a secure perimeter around the organization’s network. This guarantees that only authorized people and devices will access your data and application. Cybersecurity Mesh Architecture requires the application of security policies at the identity level contrary to network level, by operating firewalls, examining IP addresses and controlling ports. This guarantees the security of resources, regardless of changes in the infrastructure.
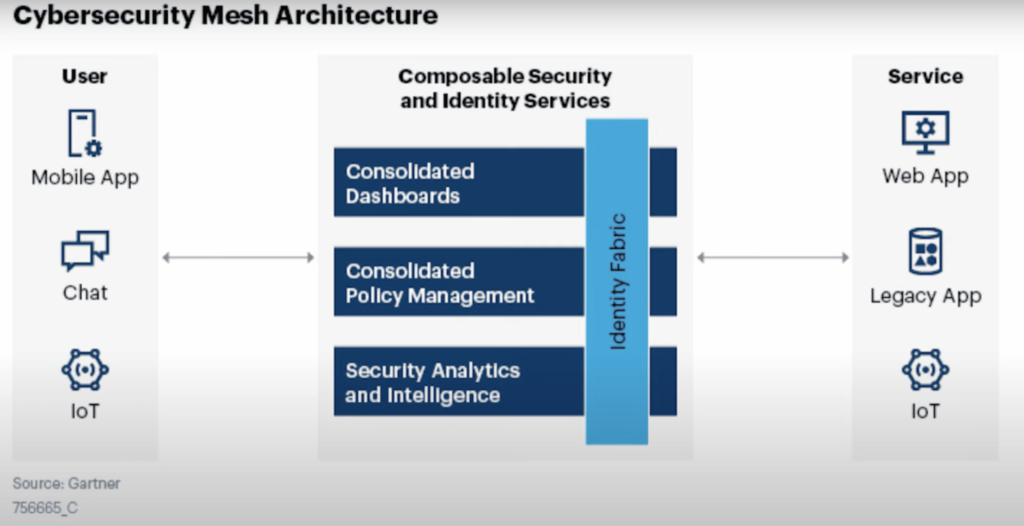
The access to each entry point is managed from a centralized authority point, which makes the CSMA security approach flexible and scalable. It works best for hybrid and multi-cloud environments, as they are accessed by various devices and apps.
The controlling stack which grants the access rights communicates with security controls at the endpoint, the cloud, for identity and access management, around apps and emails. The collaboration between the security control is facilitated by four supportive layers, which are:
Security Analytics and Intelligence
The layer consists of multiple security instruments communicating with one another. User behavior analytics spots anomalies and lowers the risk of insider attacks, as well as collects the data for following analyzes. This gives information for improvement, as the security tools will faster react to the triggers.
Consolidated Dashboards
This layer brings the team together to manage the security ecosystem. Thus the responses to the attacks can be deployed faster and the security events detected more efficiently.
Distributed Identity Fabric
This layer contains data and interrelated processes. The analytics tools continuously diagnose data points from various apps and advise where data should be used. They also specify the approved users and malicious attackers.
Consolidated Policy and Posture Management
The layer enables security specialists to identify application access policies for users and devices from the main centralized location.
All of the layers, as well as monitoring of data usage, storage, and sharing is performed through every device and user in the network.
What is vital for the CSMA approach?
While adopting the CSMA take into account the need of the platform capable of bringing all security tools used by the enterprise together to create a mesh. As well as the cooperation between the security unit and other teams within the company plays a significant role. The first thing to do while adjusting CSMA is the identity infrastructure, as the identities and access regulations of people and devices are crucial to this security environment.
Another thing to consider is the strong policy management, especially at least-privilege access policies
Also, CSMA requires strong centralized policy management and governance. It will be important to organize access policies with the least privileges, which organizations can achieve by using a centralized policy management mechanism combined with distributed enforcement. To create an integrated security it is recommended to apply AI and machine-learning policies to the identity layer and extend them throughout the access path.
If you still have doubts about Cybersecurity Mesh Architecture
CSMA integrates all security tools together and protects your network regardless of where your users come from or from what location your employees work. This gives your fintech company a number of advantages such as:
– Integration facilities are more efficient in response to security risks that may and will occur in the future, as the cyberattacks become more sophisticated. The plug-in APIs within CSMA provide you with analytics and customization tools.
– While using Cybersecurity Mesh Architecture you may discover and close the gaps in the security mechanism. Your system becomes more secure as a whole, while currently used security tools are mostly siloed.
– The supportive layers, such as security analytics, identity fabric, policy management, and integrated dashboards make a strong security solution, which is centralized and can be managed by a single person or small team, which may reduce the cost of security measures.